$ grep kermit /etc/services
kermit 1649/tcp
ssh command you already know). Now you could easily log in to a machine and exchange files with it without missing a beat.
And so it was that the Internet Kermit Service Daemon (IKSD) came into existence. It allows a person to set up a Kermit server, which can authenticate against local accounts or present anonymous access akin to FTP.
And so I established the quux.org Kermit Server, which runs the Unix IKSD (part of the Debian ckermit package).
$ kermit
C-Kermit 10.0 Beta.08, 15 Dec 2022, for Linux+SSL (64-bit)
Copyright (C) 1985, 2022,
Trustees of Columbia University in the City of New York.
Open Source 3-clause BSD license since 2011.
Type ? or HELP for help.
(/tmp/t/) C-Kermit>iksd /user:anonymous kermit.quux.org
DNS Lookup... Trying 135.148.101.37... Reverse DNS Lookup... (OK)
Connecting to host glockenspiel.complete.org:1649
Escape character: Ctrl-\ (ASCII 28, FS): enabled
Type the escape character followed by C to get back,
or followed by ? to see other options.
----------------------------------------------------
>>> Welcome to the Internet Kermit Service at kermit.quux.org <<<
To log in, use 'anonymous' as the username, and any non-empty password
Internet Kermit Service ready at Fri Aug 4 22:32:17 2023
C-Kermit 10.0 Beta.08, 15 Dec 2022
kermit
Enter e-mail address as Password: [redacted]
Anonymous login.
You are now connected to the quux kermit server.
Try commands like HELP, cd gopher, dir, and the like. Use INTRO
for a nice introduction.
(~/) IKSD>
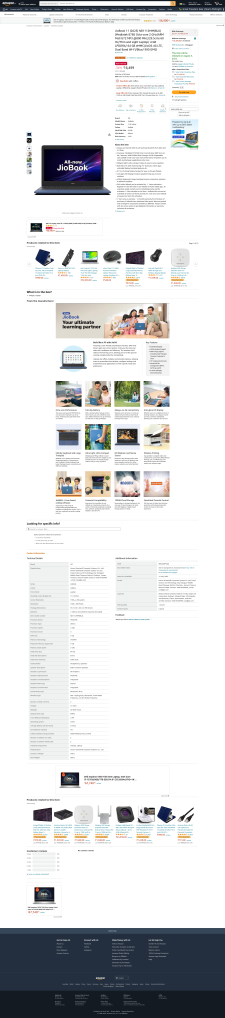
 About a week back Jio launched a laptop called JioBook that will be manufactured in China
About a week back Jio launched a laptop called JioBook that will be manufactured in China

 Unlike the Americans who chose the path to have more competition, we have chosen the path to have more monopolies. So even though, I very much liked Louis es project sooner or later finding the devices itself would be hard. While the recent notification is for laptops, what stops them from doing the same with mobiles or even desktop systems. As it is, both smartphones as well as desktop systems has been contracting since last year as food inflation has gone up.
Add to that availability of products has been made scarce (whether by design or not, unknown.) The end result, the latest processor launched overseas becomes the new thing here 3-4 years later. And that was before this notification. This will only decrease competition and make Ambanis rich at cost of everyone else. So much for east of doing business . Also the backlash has been pretty much been tepid. So what I shared will probably happen again sooner or later.
The only interesting thing is that it s based on Android, probably in part due to the issues people seeing in both Windows 10, 11 and whatnot.
Till later.
Update :- The print tried a decluttering but instead cluttered the topic. While what he shared all was true, and certainly it is a step backwards but he didn t need to show how most Indians had to go to RBI for the same. I remember my Mamaji doing the same and sharing afterwards that all he had was $100 for a day which while being a big sum was paltry if you were staying in a hotel and were there for company business. He survived on bananas and whatver cheap veg. he could find then. This is almost 35-40 odd years ago. As shared the Govt. has been doing missteps for quite sometime now. The print does try to take a balanced take so it doesn t run counter of the Government but even it knows that this is a bad take. The whole thing about security is just laughable, did they wake up after 9 years. And now in its own wisdom it apparently has shifted the ban instead from now to 3 months afterwards. Of course, most people on the right just applauding without understanding the complexities and implications of the same. Vendors like Samsung and Apple who have made assembly operations would do a double-think and shift to Taiwan, Vietnam, Mexico anywhere. Global money follows global trends. And such missteps do not help
Unlike the Americans who chose the path to have more competition, we have chosen the path to have more monopolies. So even though, I very much liked Louis es project sooner or later finding the devices itself would be hard. While the recent notification is for laptops, what stops them from doing the same with mobiles or even desktop systems. As it is, both smartphones as well as desktop systems has been contracting since last year as food inflation has gone up.
Add to that availability of products has been made scarce (whether by design or not, unknown.) The end result, the latest processor launched overseas becomes the new thing here 3-4 years later. And that was before this notification. This will only decrease competition and make Ambanis rich at cost of everyone else. So much for east of doing business . Also the backlash has been pretty much been tepid. So what I shared will probably happen again sooner or later.
The only interesting thing is that it s based on Android, probably in part due to the issues people seeing in both Windows 10, 11 and whatnot.
Till later.
Update :- The print tried a decluttering but instead cluttered the topic. While what he shared all was true, and certainly it is a step backwards but he didn t need to show how most Indians had to go to RBI for the same. I remember my Mamaji doing the same and sharing afterwards that all he had was $100 for a day which while being a big sum was paltry if you were staying in a hotel and were there for company business. He survived on bananas and whatver cheap veg. he could find then. This is almost 35-40 odd years ago. As shared the Govt. has been doing missteps for quite sometime now. The print does try to take a balanced take so it doesn t run counter of the Government but even it knows that this is a bad take. The whole thing about security is just laughable, did they wake up after 9 years. And now in its own wisdom it apparently has shifted the ban instead from now to 3 months afterwards. Of course, most people on the right just applauding without understanding the complexities and implications of the same. Vendors like Samsung and Apple who have made assembly operations would do a double-think and shift to Taiwan, Vietnam, Mexico anywhere. Global money follows global trends. And such missteps do not help 

 I've never been a fan of IoT devices for obvious reasons: not only do they tend
to be excellent at being expensive vendor locked-in machines, but far too often,
they also end up turning into e-waste after a short amount of time.
Manufacturers can go out of business or simply decide to shut down the cloud
servers for older models, and then you're stuck with a brick.
Well, this all changes today, as I've built my first IoT device and I love it.
Introducing pymonitair.
What
pymonitair is a MicroPython project that aims to display weather data from a
home weather station (like the ones sold by AirGradient) on a small display.
The source code was written for the Raspberry Pi Pico W, the
Waveshare Pico OLED 1.3 display and the RevolvAir Revo 1
weather station, but can be adapted to other displays and stations easily, as I
tried to keep the code as modular as possible.
The general MicroPython code itself isn't specific to the Raspberry Pi Pico and
shouldn't need to be modified for other boards.
pymonitair features:
I've never been a fan of IoT devices for obvious reasons: not only do they tend
to be excellent at being expensive vendor locked-in machines, but far too often,
they also end up turning into e-waste after a short amount of time.
Manufacturers can go out of business or simply decide to shut down the cloud
servers for older models, and then you're stuck with a brick.
Well, this all changes today, as I've built my first IoT device and I love it.
Introducing pymonitair.
What
pymonitair is a MicroPython project that aims to display weather data from a
home weather station (like the ones sold by AirGradient) on a small display.
The source code was written for the Raspberry Pi Pico W, the
Waveshare Pico OLED 1.3 display and the RevolvAir Revo 1
weather station, but can be adapted to other displays and stations easily, as I
tried to keep the code as modular as possible.
The general MicroPython code itself isn't specific to the Raspberry Pi Pico and
shouldn't need to be modified for other boards.
pymonitair features:
key0 buttonkey1 button A few weeks ago, my friend and neighbor J r me (aka lavamind)
installed a weather station on his balcony and started collecting data from it.
It has been quite useful to measure the degrading air quality during the recent
forest fires plaguing northern Canada, but sadly, the hardware itself
isn't great.
Whereas some projects like airgradient offer open hardware devices running
free software, the station we got is from RevolvAir, some kind of local
air monitoring project that aims to be a one-stop solution for exterior air
monitoring.
Not only is their device pretty expensive1, but it also reboots
frequently by itself. Even worse, their online data map requires an
account to view the data and the interface is bad, unintuitive and only stores
data up to a month.
Having a good background in data visualisation and statistics thanks to my
master's degree in economics, I decided I could do better. Two days later, I
had built a series of tools to collect, analyse and graph the JSON time series
data provided by the device.
The result is a very simple website that works without any JavaScript,
leveraging static graphs built using R. Modern web libraries and projects
offer an incredible wealth of tools to graph and visualise data, but as for
most of my web projects, I wanted something static and simple.
The source code for the project can be found here, and although it is
somewhat specific to the data structure provided by the RevolvAir device, it
could easily be adapted to other devices, as they tend to have very similar
JSON dumps.
A few weeks ago, my friend and neighbor J r me (aka lavamind)
installed a weather station on his balcony and started collecting data from it.
It has been quite useful to measure the degrading air quality during the recent
forest fires plaguing northern Canada, but sadly, the hardware itself
isn't great.
Whereas some projects like airgradient offer open hardware devices running
free software, the station we got is from RevolvAir, some kind of local
air monitoring project that aims to be a one-stop solution for exterior air
monitoring.
Not only is their device pretty expensive1, but it also reboots
frequently by itself. Even worse, their online data map requires an
account to view the data and the interface is bad, unintuitive and only stores
data up to a month.
Having a good background in data visualisation and statistics thanks to my
master's degree in economics, I decided I could do better. Two days later, I
had built a series of tools to collect, analyse and graph the JSON time series
data provided by the device.
The result is a very simple website that works without any JavaScript,
leveraging static graphs built using R. Modern web libraries and projects
offer an incredible wealth of tools to graph and visualise data, but as for
most of my web projects, I wanted something static and simple.
The source code for the project can be found here, and although it is
somewhat specific to the data structure provided by the RevolvAir device, it
could easily be adapted to other devices, as they tend to have very similar
JSON dumps.

 Like each month, have a look at the work funded by Freexian s Debian LTS offering.
Like each month, have a look at the work funded by Freexian s Debian LTS offering.
 I m six months into my journey of building a business which means its time to reflect and review the goals I set for the year.
I m six months into my journey of building a business which means its time to reflect and review the goals I set for the year.
A personal reflection on how I moved from my Debian home to find two new homes with Trisquel and Guix for my own ethical computing, and while doing so settled my dilemma about further Debian contributions.
Debian s contributions to the free software community has been tremendous. Debian was one of the early distributions in the 1990 s that combined the GNU tools (compiler, linker, shell, editor, and a set of Unix tools) with the Linux kernel and published a free software operating system. Back then there were little guidance on how to publish free software binaries, let alone entire operating systems. There was a lack of established community processes and conflict resolution mechanisms, and lack of guiding principles to motivate the work. The community building efforts that came about in parallel with the technical work has resulted in a steady flow of releases over the years.
From the work of Richard Stallman and the Free Software Foundation (FSF) during the 1980 s and early 1990 s, there was at the time already an established definition of free software. Inspired by free software definition, and a belief that a social contract helps to build a community and resolve conflicts, Debian s social contract (DSC) with the free software community was published in 1997. The DSC included the Debian Free Software Guidelines (DFSG), which directly led to the Open Source Definition.
 One of my earlier Slackware install disk sets, kept for nostalgic reasons.
One of my earlier Slackware install disk sets, kept for nostalgic reasons.contrib/non-free section and permitting use of the bug tracker to help resolve issues with non-free works. This is all explained in the social contract. There has always been a clear boundary between free and non-free work, and there has been a commitment that the Debian system itself would be 100% free.
The concern that RedHat Linux was not 100% free software was not critical to me at the time: I primarily (and happily) ran GNU tools on Solaris, IRIX, AIX, OS/2, Windows etc. Running GNU tools on RedHat Linux was an improvement, and I hadn t realized it was possible to get rid of all non-free software on my own primary machine. Debian realized that goal for me. I ve been a believer in that model ever since. I can use Solaris, macOS, Android etc knowing that I have the option of using a 100% free Debian.
While the inclusive approach towards non-free software invite and deserve criticism (some argue that being inclusive to non-inclusive behavior is a bad idea), I believe that Debian s approach was a successful survival technique: by being inclusive to and a compromise between free and non-free communities, Debian has been able to stay relevant and contribute to both environments. If Debian had not served and contributed to the free community, I believe free software people would have stopped contributing. If Debian had rejected non-free works completely, I don t think the successful Ubuntu distribution would have been based on Debian.
I wrote the majority of the text above back in September 2022, intending to post it as a way to argue for my proposal to maintain the status quo within Debian. I didn t post it because I felt I was saying the obvious, and that the obvious do not need to be repeated, and the rest of the post was just me going down memory lane.
The Debian project has been a sustainable producer of a 100% free OS up until Debian 11 bullseye. In the resolution on non-free firmware the community decided to leave the model that had resulted in a 100% free Debian for so long. The goal of Debian is no longer to publish a 100% free operating system, instead this was added: The Debian official media may include firmware . Indeed the Debian 12 bookworm release has confirmed that this would not only be an optional possibility. The Debian community could have published a 100% free Debian, in parallel with the non-free Debian, and still be consistent with their newly adopted policy, but chose not to. The result is that Debian s policies are not consistent with their actions. It doesn t make sense to claim that Debian is 100% free when the Debian installer contains non-free software. Actions speaks louder than words, so I m left reading the policies as well-intended prose that is no longer used for guidance, but for the peace of mind for people living in ivory towers. And to attract funding, I suppose.
So how to deal with this, on a personal level? I did not have an answer to that back in October 2022 after the vote. It wasn t clear to me that I would ever want to contribute to Debian under the new social contract that promoted non-free software. I went on vacation from any Debian work. Meanwhile Debian 12 bookworm was released, confirming my fears. I kept coming back to this text, and my only take-away was that it would be unethical for me to use Debian on my machines. Letting actions speak for themselves, I switched to PureOS on my main laptop during October, barely noticing any difference since it is based on Debian 11 bullseye. Back in December, I bought a new laptop and tried Trisquel and Guix on it, as they promise a migration path towards ppc64el that PureOS do not.
While I pondered how to approach my modest Debian contributions, I set out to learn Trisquel and gained trust in it. I migrated one Debian machine after another to Trisquel, and started to use Guix on others. Migration was easy because Trisquel is based on Ubuntu which is based on Debian. Using Guix has its challenges, but I enjoy its coherant documented environment. All of my essential self-hosted servers (VM hosts, DNS, e-mail, WWW, Nextcloud, CI/CD builders, backup etc) uses Trisquel or Guix now. I ve migrated many GitLab CI/CD rules to use Trisquel instead of Debian, to have a more ethical computing base for software development and deployment. I wish there were official Guix docker images around.
Time has passed, and when I now think about any Debian contributions, I m a little less muddled by my disappointment of the exclusion of a 100% free Debian. I realize that today I can use Debian in the same way that I use macOS, Android, RHEL or Ubuntu. And what prevents me from contributing to free software on those platforms? So I will make the occasional Debian contribution again, knowing that it will also indirectly improve Trisquel. To avoid having to install Debian, I need a development environment in Trisquel that allows me to build Debian packages. I have found a recipe for doing this:
# System commands:
How to sustainably deliver a 100% free software binary distributions seems like an open question, and the challenges are not all that different compared to the 1990 s or early 2000 s. I m hoping Debian will come back to provide a 100% free platform, but my fear is that Debian will compromise even further on the free software ideals rather than the opposite. With similar arguments that were used to add the non-free firmware, Debian could compromise the free software spirit of the Linux boot process (e.g., non-free boot images signed by Debian) and media handling (e.g., web browsers and DRM), as Debian have already done with appstore-like functionality for non-free software (Python pip). To learn about other freedom issues in Debian packaging, browsing Trisquel s helper scripts may enlight you.
Debian s setback and the recent setback for RHEL-derived distributions are sad, and it will be a challenge for these communities to find internally consistent coherency going forward. I wish them the best of luck, as Debian and RHEL are important for the wider free software eco-system. Let s see how the community around Trisquel, Guix and the other FSDG-distributions evolve in the future.
The situation for free software today appears better than it was years ago regardless of Debian and RHEL s setbacks though, which is important to remember! I don t recall being able install a 100% free OS on a modern laptop and modern server as easily as I am able to do today.
Happy Hacking!
Addendum 22 July 2023: The original title of this post was Coping with non-free Debian, and there was a thread about it that included feedback on the title. I do agree that my initial title was confrontational, and I ve changed it to the more specific Coping with non-free software in Debian. I do appreciate all the fine free software that goes into Debian, and hope that this will continue and improve, although I have doubts given the opinions expressed by the majority of developers. For the philosophically inclined, it is interesting to think about what it means to say that a compilation of software is freely licensed. At what point does a compilation of software deserve the labels free vs non-free? Windows probably contains some software that is published as free software, let s say Windows is 1% free. Apple authors a lot of free software (as a tangent, Apple probably produce more free software than what Debian as an organization produces), and let s say macOS contains 20% free software. Solaris (or some still maintained derivative like OpenIndiana) is mostly freely licensed these days, isn t it? Let s say it is 80% free. Ubuntu and RHEL pushes that closer to let s say 95% free software. Debian used to be 100% but is now slightly less at maybe 99%. Trisquel and Guix are at 100%. At what point is it reasonable to call a compilation free? Does Debian deserve to be called freely licensed? Does macOS? Is it even possible to use these labels for compilations in any meaningful way? All numbers just taken from thin air. It isn t even clear how this can be measured (binary bytes? lines of code? CPU cycles? etc). The caveat about license review mistakes applies. I ignore Debian s own claims that Debian is 100% free software, which I believe is inconsistent and no longer true under any reasonable objective analysis. It was not true before the firmware vote since Debian ships with non-free blobs in the Linux kernel for example.
sudo apt-get install debhelper git-buildpackage debian-archive-keyring
sudo wget -O /usr/share/debootstrap/scripts/debian-common https://sources.debian.org/data/main/d/debootstrap/1.0.128%2Bnmu2/scripts/debian-common
sudo wget -O /usr/share/debootstrap/scripts/sid https://sources.debian.org/data/main/d/debootstrap/1.0.128%2Bnmu2/scripts/sid
# Run once to create build image:
DIST=sid git-pbuilder create --mirror http://deb.debian.org/debian/ --debootstrapopts "--exclude=usr-is-merged" --basepath /var/cache/pbuilder/base-sid.cow
# Run in a directory with debian/ to build a package:
gbp buildpackage --git-pbuilder --git-dist=sid
| Series: | Semiosis #1 |
| Publisher: | Tor |
| Copyright: | February 2018 |
| ISBN: | 0-7653-9137-6 |
| Format: | Kindle |
| Pages: | 333 |
 After holding the domain copyninja.info for almost 15 years, I finally let it
expire and bought a new domain, copyninja.in. With this move, I also bid
goodbye to my VPS, which I had been using for over 12 years on DigitalOcean.
This particular VPS was initially set up with Debian Wheezy (7) and had been
upgraded over the years to successive Debian versions and finally was running
Debian Bullseye (11).
The main reason for the move was that the .info domain was becoming more
expensive every year, and the VPS, which I had upgraded to the $10 USD range,
cost around $12 USD per month with GST included. Since I wasn't really using the
VPS anymore and had recently even broken my DNS and mail server settings, I
decided it was the right time to reduce this additional cost.
Now I have a cheaper .in domain, and the VPS is on a minimal configuration at
DigitalOcean, costing $5 USD per month (which becomes almost $7 USD with GST).
Currently, I only run a blog and mail server on this VPS. I will assess if I
really need to keep running the mail server for some more time. If not, I will
move the blog to a hosting service like GitHub Pages and completely get rid of
the VPS.
My email address has now changed, and the new mail can be obtained from this
link <http://scr.im/newcopyninj>. I have updated my GPG key and added the new
email as the new UID. I still need to revoke the old domain UID. The key has
already been updated in the Debian Keyring.
After holding the domain copyninja.info for almost 15 years, I finally let it
expire and bought a new domain, copyninja.in. With this move, I also bid
goodbye to my VPS, which I had been using for over 12 years on DigitalOcean.
This particular VPS was initially set up with Debian Wheezy (7) and had been
upgraded over the years to successive Debian versions and finally was running
Debian Bullseye (11).
The main reason for the move was that the .info domain was becoming more
expensive every year, and the VPS, which I had upgraded to the $10 USD range,
cost around $12 USD per month with GST included. Since I wasn't really using the
VPS anymore and had recently even broken my DNS and mail server settings, I
decided it was the right time to reduce this additional cost.
Now I have a cheaper .in domain, and the VPS is on a minimal configuration at
DigitalOcean, costing $5 USD per month (which becomes almost $7 USD with GST).
Currently, I only run a blog and mail server on this VPS. I will assess if I
really need to keep running the mail server for some more time. If not, I will
move the blog to a hosting service like GitHub Pages and completely get rid of
the VPS.
My email address has now changed, and the new mail can be obtained from this
link <http://scr.im/newcopyninj>. I have updated my GPG key and added the new
email as the new UID. I still need to revoke the old domain UID. The key has
already been updated in the Debian Keyring.

 Like each month, have a look at the work funded by Freexian s Debian LTS offering.
Like each month, have a look at the work funded by Freexian s Debian LTS offering.
 [Note: the original version of this post named the author of the referenced blog post, and the tone of my writing could be construed to be mocking or otherwise belittling them.
While that was not my intention, I recognise that was a possible interpretation, and I have revised this post to remove identifying information and try to neutralise the tone.
On the other hand, I have kept the identifying details of the domain involved, as there are entirely legitimate security concerns that result from the issues discussed in this post.]
I have spoken before about why it is tricky to redact private keys.
Although that post demonstrated a real-world, presumably-used-in-the-wild private key, I ve been made aware of commentary along the lines of this representative sample:
[Note: the original version of this post named the author of the referenced blog post, and the tone of my writing could be construed to be mocking or otherwise belittling them.
While that was not my intention, I recognise that was a possible interpretation, and I have revised this post to remove identifying information and try to neutralise the tone.
On the other hand, I have kept the identifying details of the domain involved, as there are entirely legitimate security concerns that result from the issues discussed in this post.]
I have spoken before about why it is tricky to redact private keys.
Although that post demonstrated a real-world, presumably-used-in-the-wild private key, I ve been made aware of commentary along the lines of this representative sample:
I find it hard to believe that anyone would take their actual production key and redact it for documentation. Does the author have evidence of this in practice, or did they see example keys and assume they were redacted production keys?Well, buckle up, because today s post is another real-world case study, with rather higher stakes than the previous example.
xs.
Based on the steps I explained previously, it is relatively straightforward to retrieve the entire, intact private key.
72bef096997ec59a671d540d75bd1926363b2097eb9fe10220b2654b1f665b54
Searching for certificates which use that key fingerprint, we find one result: a certificate for hiltonhotels.jp (and a bunch of other, related, domains, as subjectAltNames).
As of the time of writing, that certificate is not marked as revoked, and appears to be the same certificate that is currently presented to visitors of that site.
This is, shall we say, not great.
Anyone in possession of this private key which, I should emphasise, has presumably been public information since the post s publication date of February 2023 has the ability to completely transparently impersonate the sites listed in that certificate.
That would provide an attacker with the ability to capture any data a user entered, such as personal information, passwords, or payment details, and also modify what the user s browser received, including injecting malware or other unpleasantness.
In short, no good deed goes unpunished, and this attempt to educate the world at large about the benefits of secure key storage has instead published private key material.
Remember, kids: friends don t let friends post redacted private keys to the Internet.
 I m calling time on DNSSEC. Last week, prompted by a change in my DNS hosting setup, I began removing it from the few personal zones I had signed. Then this Monday the .nz ccTLD experienced a multi-day availability incident triggered by the annual DNSSEC key rotation process. This incident broke several of my unsigned zones, which led me to say very unkind things about DNSSEC on Mastodon and now I feel compelled to more completely explain my thinking:
For almost all domains and use-cases, the costs and risks of deploying DNSSEC outweigh the benefits it provides. Don t bother signing your zones.
The .nz incident, while topical, is not the motivation or the trigger for this conclusion. Had it been a novel incident, it would still have been annoying, but novel incidents are how we learn so I have a small tolerance for them. The problem with DNSSEC is precisely that this incident was not novel, just the latest in a long and growing list.
It s a clear pattern. DNSSEC is complex and risky to deploy. Choosing to sign your zone will almost inevitably mean that you will experience lower availability for your domain over time than if you leave it unsigned. Even if you have a team of DNS experts maintaining your zone and DNS infrastructure, the risk of routine operational tasks triggering a loss of availability (unrelated to any attempted attacks that DNSSEC may thwart) is very high - almost guaranteed to occur. Worse, because of the nature of DNS and DNSSEC these incidents will tend to be prolonged and out of your control to remediate in a timely fashion.
The only benefit you get in return for accepting this almost certain reduction in availability is trust in the integrity of the DNS data a subset of your users (those who validate DNSSEC) receive. Trusted DNS data that is then used to communicate across an untrusted network layer. An untrusted network layer which you are almost certainly protecting with TLS which provides a more comprehensive and trustworthy set of security guarantees than DNSSEC is capable of, and provides those guarantees to all your users regardless of whether they are validating DNSSEC or not.
In summary, in our modern world where TLS is ubiquitous, DNSSEC provides only a thin layer of redundant protection on top of the comprehensive guarantees provided by TLS, but adds significant operational complexity, cost and a high likelihood of lowered availability.
In an ideal world, where the deployment cost of DNSSEC and the risk of DNSSEC-induced outages were both low, it would absolutely be desirable to have that redundancy in our layers of protection. In the real world, given the DNSSEC protocol we have today, the choice to avoid its complexity and rely on TLS alone is not at all painful or risky to make as the operator of an online service. In fact, it s the prudent choice that will result in better overall security outcomes for your users.
Ignore DNSSEC and invest the time and resources you would have spent deploying it improving your TLS key and certificate management.
Ironically, the one use-case where I think a valid counter-argument for this position can be made is TLDs (including ccTLDs such as .nz). Despite its many failings, DNSSEC is an Internet Standard, and as infrastructure providers, TLDs have an obligation to enable its use. Unfortunately this means that everyone has to bear the costs, complexities and availability risks that DNSSEC burdens these operators with. We can t avoid that fact, but we can avoid creating further costs, complexities and risks by choosing not to deploy DNSSEC on the rest of our non-TLD zones.
I m calling time on DNSSEC. Last week, prompted by a change in my DNS hosting setup, I began removing it from the few personal zones I had signed. Then this Monday the .nz ccTLD experienced a multi-day availability incident triggered by the annual DNSSEC key rotation process. This incident broke several of my unsigned zones, which led me to say very unkind things about DNSSEC on Mastodon and now I feel compelled to more completely explain my thinking:
For almost all domains and use-cases, the costs and risks of deploying DNSSEC outweigh the benefits it provides. Don t bother signing your zones.
The .nz incident, while topical, is not the motivation or the trigger for this conclusion. Had it been a novel incident, it would still have been annoying, but novel incidents are how we learn so I have a small tolerance for them. The problem with DNSSEC is precisely that this incident was not novel, just the latest in a long and growing list.
It s a clear pattern. DNSSEC is complex and risky to deploy. Choosing to sign your zone will almost inevitably mean that you will experience lower availability for your domain over time than if you leave it unsigned. Even if you have a team of DNS experts maintaining your zone and DNS infrastructure, the risk of routine operational tasks triggering a loss of availability (unrelated to any attempted attacks that DNSSEC may thwart) is very high - almost guaranteed to occur. Worse, because of the nature of DNS and DNSSEC these incidents will tend to be prolonged and out of your control to remediate in a timely fashion.
The only benefit you get in return for accepting this almost certain reduction in availability is trust in the integrity of the DNS data a subset of your users (those who validate DNSSEC) receive. Trusted DNS data that is then used to communicate across an untrusted network layer. An untrusted network layer which you are almost certainly protecting with TLS which provides a more comprehensive and trustworthy set of security guarantees than DNSSEC is capable of, and provides those guarantees to all your users regardless of whether they are validating DNSSEC or not.
In summary, in our modern world where TLS is ubiquitous, DNSSEC provides only a thin layer of redundant protection on top of the comprehensive guarantees provided by TLS, but adds significant operational complexity, cost and a high likelihood of lowered availability.
In an ideal world, where the deployment cost of DNSSEC and the risk of DNSSEC-induced outages were both low, it would absolutely be desirable to have that redundancy in our layers of protection. In the real world, given the DNSSEC protocol we have today, the choice to avoid its complexity and rely on TLS alone is not at all painful or risky to make as the operator of an online service. In fact, it s the prudent choice that will result in better overall security outcomes for your users.
Ignore DNSSEC and invest the time and resources you would have spent deploying it improving your TLS key and certificate management.
Ironically, the one use-case where I think a valid counter-argument for this position can be made is TLDs (including ccTLDs such as .nz). Despite its many failings, DNSSEC is an Internet Standard, and as infrastructure providers, TLDs have an obligation to enable its use. Unfortunately this means that everyone has to bear the costs, complexities and availability risks that DNSSEC burdens these operators with. We can t avoid that fact, but we can avoid creating further costs, complexities and risks by choosing not to deploy DNSSEC on the rest of our non-TLD zones.
| Series: | Discworld #29 |
| Publisher: | Harper |
| Copyright: | November 2002 |
| Printing: | August 2014 |
| ISBN: | 0-06-230740-1 |
| Format: | Mass market |
| Pages: | 451 |
Keep the peace. That was the thing. People often failed to understand what that meant. You'd go to some life-threatening disturbance like a couple of neighbors scrapping in the street over who owned the hedge between their properties, and they'd both be bursting with aggrieved self-righteousness, both yelling, their wives would either be having a private scrap on the side or would have adjourned to a kitchen for a shared pot of tea and a chat, and they all expected you to sort it out. And they could never understand that it wasn't your job. Sorting it out was a job for a good surveyor and a couple of lawyers, maybe. Your job was to quell the impulse to bang their stupid fat heads together, to ignore the affronted speeches of dodgy self-justification, to get them to stop shouting and to get them off the street. Once that had been achieved, your job was over. You weren't some walking god, dispensing finely tuned natural justice. Your job was simply to bring back peace.When Vimes is thrown back in time, he has to pick up the role of his own mentor, the person who taught him what policing should be like. His younger self is right there, watching everything he does, and he's desperately afraid he'll screw it up and set a worse example. Make history worse when he's trying to make it better. It's a beautifully well-done bit of tension that uses time travel as the hook to show both how difficult mentorship is and also how irritating one's earlier naive self would be.
He wondered if it was at all possible to give this idiot some lessons in basic politics. That was always the dream, wasn't it? "I wish I'd known then what I know now"? But when you got older you found out that you now wasn't you then. You then was a twerp. You then was what you had to be to start out on the rocky road of becoming you now, and one of the rocky patches on that road was being a twerp.The backdrop of this story, as advertised by the map at the front of the book, is a revolution of sorts. And the revolution does matter, but not in the obvious way. It creates space and circumstance for some other things to happen that are all about the abuse of policing as a tool of politics rather than Vimes's principle of keeping the peace. I mentioned when reviewing Men at Arms that it was an awkward book to read in the United States in 2020. This book tackles the ethics of policing head-on, in exactly the way that book didn't. It's also a marvelous bit of competence porn. Somehow over the years, Vimes has become extremely good at what he does, and not just in the obvious cop-walking-a-beat sort of ways. He's become a leader. It's not something he thinks about, even when thrown back in time, but it's something Pratchett can show the reader directly, and have the other characters in the book comment on. There is so much more that I'd like to say, but so much would be spoilers, and I think Night Watch is more effective when you have the suspense of slowly puzzling out what's going to happen. Pratchett's pacing is exquisite. It's also one of the rare Discworld novels where Pratchett fully commits to a point of view and lets Vimes tell the story. There are a few interludes with other people, but the only other significant protagonist is, quite fittingly, Vetinari. I won't say anything more about that except to note that the relationship between Vimes and Vetinari is one of the best bits of fascinating subtlety in all of Discworld. I think it's also telling that nothing about Night Watch reads as parody. Sure, there is a nod to Back to the Future in the lightning storm, and it's impossible to write a book about police and street revolutions without making the reader think about Les Miserables, but nothing about this plot matches either of those stories. This is Pratchett telling his own story in his own world, unapologetically, and without trying to wedge it into parody shape, and it is so much the better book for it. The one quibble I have with the book is that the bits with the Time Monks don't really work. Lu-Tze is annoying and flippant given the emotional stakes of this story, the interludes with him are frustrating and out of step with the rest of the book, and the time travel hand-waving doesn't add much. I see structurally why Pratchett put this in: it gives Vimes (and the reader) a time frame and a deadline, it establishes some of the ground rules and stakes, and it provides a couple of important opportunities for exposition so that the reader doesn't get lost. But it's not good story. The rest of the book is so amazingly good, though, that it doesn't matter (and the framing stories for "what if?" explorations almost never make much sense). The other thing I have a bit of a quibble with is outside the book. Night Watch, as you may have guessed by now, is the origin of the May 25th Pratchett memes that you will be familiar with if you've spent much time around SFF fandom. But this book is dramatically different from what I was expecting based on the memes. You will, for example see a lot of people posting "Truth, Justice, Freedom, Reasonably Priced Love, And a Hard-Boiled Egg!", and before reading the book it sounds like a Pratchett-style humorous revolutionary slogan. And I guess it is, sort of, but, well... I have to quote the scene:
"You'd like Freedom, Truth, and Justice, wouldn't you, Comrade Sergeant?" said Reg encouragingly. "I'd like a hard-boiled egg," said Vimes, shaking the match out. There was some nervous laughter, but Reg looked offended. "In the circumstances, Sergeant, I think we should set our sights a little higher " "Well, yes, we could," said Vimes, coming down the steps. He glanced at the sheets of papers in front of Reg. The man cared. He really did. And he was serious. He really was. "But...well, Reg, tomorrow the sun will come up again, and I'm pretty sure that whatever happens we won't have found Freedom, and there won't be a whole lot of Justice, and I'm damn sure we won't have found Truth. But it's just possible that I might get a hard-boiled egg."I think I'm feeling defensive of the heart of this book because it's such an emotional gut punch and says such complicated and nuanced things about politics and ethics (and such deeply cynical things about revolution). But I think if I were to try to represent this story in a meme, it would be the "angels rise up" song, with all the layers of meaning that it gains in this story. I'm still at the point where the lilac sprigs remind me of Sergeant Colon becoming quietly furious at the overstep of someone who wasn't there. There's one other thing I want to say about that scene: I'm not naturally on Vimes's side of this argument. I think it's important to note that Vimes's attitude throughout this book is profoundly, deeply conservative. The hard-boiled egg captures that perfectly: it's a bit of physical comfort, something you can buy or make, something that's part of the day-to-day wheels of the city that Vimes talks about elsewhere in Night Watch. It's a rejection of revolution, something that Vimes does elsewhere far more explicitly. Vimes is a cop. He is in some profound sense a defender of the status quo. He doesn't believe things are going to fundamentally change, and it's not clear he would want them to if they did. And yet. And yet, this is where Pratchett's Dickensian morality comes out. Vimes is a conservative at heart. He's grumpy and cynical and jaded and he doesn't like change. But if you put him in a situation where people are being hurt, he will break every rule and twist every principle to stop it.
He wanted to go home. He wanted it so much that he trembled at the thought. But if the price of that was selling good men to the night, if the price was filling those graves, if the price was not fighting with every trick he knew... then it was too high. It wasn't a decision that he was making, he knew. It was happening far below the areas of the brain that made decisions. It was something built in. There was no universe, anywhere, where a Sam Vimes would give in on this, because if he did then he wouldn't be Sam Vimes any more.This is truly exceptional stuff. It is the best Discworld novel I have read, by far. I feel like this was the Watch novel that Pratchett was always trying to write, and he had to write five other novels first to figure out how to write it. And maybe to prepare Discworld readers to read it. There are a lot of Discworld novels that are great on their own merits, but also it is 100% worth reading all the Watch novels just so that you can read this book. Followed in publication order by The Wee Free Men and later, thematically, by Thud!. Rating: 10 out of 10
| Publisher: | Tordotcom |
| Copyright: | 2022 |
| ISBN: | 1-250-21097-6 |
| Format: | Kindle |
| Pages: | 340 |
| Series: | Fall Revolution #2 |
| Publisher: | Tor |
| Copyright: | 1996 |
| Printing: | January 2001 |
| ISBN: | 0-8125-6864-8 |
| Format: | Mass market |
| Pages: | 339 |

 Like each month, have a look at the work funded by Freexian s Debian LTS offering.
Like each month, have a look at the work funded by Freexian s Debian LTS offering.
 This isn't a book review, although the reason that I am typing this now is
because of a book, You Are Not Alone: from the creator and host of
Griefcast, Cariad Lloyd, ISBN: 978-1526621870 and I include a handful of
quotes from Cariad where there is really no better way of describing things.
Many people experience death for the first time as a child, often relating to a
family pet. Death is universal but every experience of death is unique. One of
the myths of grief is the idea of the Five Stages but this is a
misinterpretation. Denial, Anger, Bargaining, Depression and Acceptance
represent the five stage model of death and have nothing to do with
grief. The five stages were developed from studying those who are
terminally ill, the dying, not those who then grieve for the dead person and
have to go on living without them. Grief is for those who loved the person who
has died and it varies between each of those people just as people vary in how
they love someone. The Five Stages end at the moment of death, grief is what
comes next and most people do not grieve in stages, it can be more like a
tangled knot.
Death has a date and time, so that is why the last stage of the model is
Acceptance. Grief has no timetable, those who grieve will carry that grief for
the rest of their lives. Death starts the process of grief in those who go on
living just as it ends the life of the person who is loved. "Grief eases and
changes and returns but it never disappears.".
I suspect many will have already stopped reading by this point. People do not
talk about death and grief enough and this only adds to the burden of those who
carry their grief. It can be of enormous comfort to those who have carried
grief for some time to talk directly about the dead, not in vague pleasantries
but with specific and strong memories. Find a safe place without distractions
and talk with the person grieving face to face. Name the dead person. Go to
places with strong memories and be there alongside. Talk about the times with
that person before their death. Early on, everything about grief is painful and
sad. It does ease but it remains unpredictable. Closing it away in a box inside
your head (as I did at one point) is like cutting off a damaged limb but
keeping the pain in a box on the shelf. You still miss the limb and eventually,
the box starts leaking.
For me, there were family pets which died but my first job out of university
was to work in hospitals, helping the nurses manage the medication regimen and
providing specialist advice as a pharmacist. It will not be long in that
environment before everyone on the ward gets direct experience of the death of
a person. In some ways, this helped me to separate the process of death from
the process of grief. I cared for these people as patients but these were not
my loved ones. Later, I worked in specialist terminal care units, including
providing potential treatments as part of clinical trials. Here, it was not
expected for any patient to be discharged alive. The more aggressive
chemotherapies had already been tried and had failed, this was about pain
relief, symptom management and helping the loved ones. Palliative care is not
just about the patient, it involves helping the loved ones to accept what is
happening as this provides comfort to the patient by closing the loop.
Grief is stressful. One of the most common causes of personal stress is
bereavement.
The death of your loved one is outside of your control, it has happened, no
amount of regret can change that. Then come all the other stresses, maybe about
money or having somewhere to live as a result of what else has changed after
the death or having to care for other loved ones.
In the early stages, the first two years, I found it helpful to imagine my life
as a box containing a ball and a button. The button triggers new waves of pain
and loss each time it is hit. The ball bounces around the box and hits the
button at random. Initially, the button is large and the ball is enormous, so
the button is hit almost constantly. Over time, both the button and the ball
change size. Starting off at maximum, initially there is only one direction of
change. There are two problems with this analogy. First is that the grief ball
has infinite energy which does not happen in reality. The ball may get smaller
and the button harder to hit but the ball will continue bouncing. Secondly, the
life box is not a predictable shape, so the pattern of movement of the ball is
unpredictable.
A single stress is one thing, but what has happened since has just kept adding
more stress for me. Shortly before my father died 5 years ago now, I had moved
house. Then, I was made redundant on the day of the first anniversary of my
father's death. A year or so later, my long term relationship failed and a few
months after that COVID-19 appeared. As the country eased out of the pandemic
in 2021, my mother died (unrelated to COVID itself). A year after that, I had
to take early retirement. My brother and sister, of course, share a lot of
those stressors. My brother, in particular, took the responsibility for
organising both funerals and did most of the visits to my mother before her
death. The grief is different for each of the surviving family.
Cariad's book helped me understand why I was getting frequent ideas about going
back to visit places which my father and I both knew. My parents encouraged
each of us to work hard to leave Port Talbot (or Pong Toilet locally) behind,
in no small part due to the unrestrained pollution and deprivation that is
common to small industrial towns across Wales, the midlands and the north of
the UK. It wasn't that I wanted to move house back to our ancestral roots. It
was my grief leaking out of the box. Yes, I long for mountains and the sea
because I'm now living in a remorselessly flat and landlocked region after
moving here for employment. However, it was my grief driving those longings -
not for the physical surroundings but out of the shared memories with my
father. I can visit those memories without moving house, I just need to arrange
things so that I can be undisturbed and undistracted.
I am not alone with my grief and I am grateful to my friends who have helped
whilst carrying their own grief. It is necessary for everyone to think and talk
about death and grief. In respect of your own death, no matter how far ahead
that may be, consider Advance Care Planning and Expressions of Wish as well
as your Will.
This isn't a book review, although the reason that I am typing this now is
because of a book, You Are Not Alone: from the creator and host of
Griefcast, Cariad Lloyd, ISBN: 978-1526621870 and I include a handful of
quotes from Cariad where there is really no better way of describing things.
Many people experience death for the first time as a child, often relating to a
family pet. Death is universal but every experience of death is unique. One of
the myths of grief is the idea of the Five Stages but this is a
misinterpretation. Denial, Anger, Bargaining, Depression and Acceptance
represent the five stage model of death and have nothing to do with
grief. The five stages were developed from studying those who are
terminally ill, the dying, not those who then grieve for the dead person and
have to go on living without them. Grief is for those who loved the person who
has died and it varies between each of those people just as people vary in how
they love someone. The Five Stages end at the moment of death, grief is what
comes next and most people do not grieve in stages, it can be more like a
tangled knot.
Death has a date and time, so that is why the last stage of the model is
Acceptance. Grief has no timetable, those who grieve will carry that grief for
the rest of their lives. Death starts the process of grief in those who go on
living just as it ends the life of the person who is loved. "Grief eases and
changes and returns but it never disappears.".
I suspect many will have already stopped reading by this point. People do not
talk about death and grief enough and this only adds to the burden of those who
carry their grief. It can be of enormous comfort to those who have carried
grief for some time to talk directly about the dead, not in vague pleasantries
but with specific and strong memories. Find a safe place without distractions
and talk with the person grieving face to face. Name the dead person. Go to
places with strong memories and be there alongside. Talk about the times with
that person before their death. Early on, everything about grief is painful and
sad. It does ease but it remains unpredictable. Closing it away in a box inside
your head (as I did at one point) is like cutting off a damaged limb but
keeping the pain in a box on the shelf. You still miss the limb and eventually,
the box starts leaking.
For me, there were family pets which died but my first job out of university
was to work in hospitals, helping the nurses manage the medication regimen and
providing specialist advice as a pharmacist. It will not be long in that
environment before everyone on the ward gets direct experience of the death of
a person. In some ways, this helped me to separate the process of death from
the process of grief. I cared for these people as patients but these were not
my loved ones. Later, I worked in specialist terminal care units, including
providing potential treatments as part of clinical trials. Here, it was not
expected for any patient to be discharged alive. The more aggressive
chemotherapies had already been tried and had failed, this was about pain
relief, symptom management and helping the loved ones. Palliative care is not
just about the patient, it involves helping the loved ones to accept what is
happening as this provides comfort to the patient by closing the loop.
Grief is stressful. One of the most common causes of personal stress is
bereavement.
The death of your loved one is outside of your control, it has happened, no
amount of regret can change that. Then come all the other stresses, maybe about
money or having somewhere to live as a result of what else has changed after
the death or having to care for other loved ones.
In the early stages, the first two years, I found it helpful to imagine my life
as a box containing a ball and a button. The button triggers new waves of pain
and loss each time it is hit. The ball bounces around the box and hits the
button at random. Initially, the button is large and the ball is enormous, so
the button is hit almost constantly. Over time, both the button and the ball
change size. Starting off at maximum, initially there is only one direction of
change. There are two problems with this analogy. First is that the grief ball
has infinite energy which does not happen in reality. The ball may get smaller
and the button harder to hit but the ball will continue bouncing. Secondly, the
life box is not a predictable shape, so the pattern of movement of the ball is
unpredictable.
A single stress is one thing, but what has happened since has just kept adding
more stress for me. Shortly before my father died 5 years ago now, I had moved
house. Then, I was made redundant on the day of the first anniversary of my
father's death. A year or so later, my long term relationship failed and a few
months after that COVID-19 appeared. As the country eased out of the pandemic
in 2021, my mother died (unrelated to COVID itself). A year after that, I had
to take early retirement. My brother and sister, of course, share a lot of
those stressors. My brother, in particular, took the responsibility for
organising both funerals and did most of the visits to my mother before her
death. The grief is different for each of the surviving family.
Cariad's book helped me understand why I was getting frequent ideas about going
back to visit places which my father and I both knew. My parents encouraged
each of us to work hard to leave Port Talbot (or Pong Toilet locally) behind,
in no small part due to the unrestrained pollution and deprivation that is
common to small industrial towns across Wales, the midlands and the north of
the UK. It wasn't that I wanted to move house back to our ancestral roots. It
was my grief leaking out of the box. Yes, I long for mountains and the sea
because I'm now living in a remorselessly flat and landlocked region after
moving here for employment. However, it was my grief driving those longings -
not for the physical surroundings but out of the shared memories with my
father. I can visit those memories without moving house, I just need to arrange
things so that I can be undisturbed and undistracted.
I am not alone with my grief and I am grateful to my friends who have helped
whilst carrying their own grief. It is necessary for everyone to think and talk
about death and grief. In respect of your own death, no matter how far ahead
that may be, consider Advance Care Planning and Expressions of Wish as well
as your Will.
Help your loved ones cope with your death by describing what you would like to happen.
Document how your life has been arranged so that the executor of your Will can find the right documents to inform:
- your bank,
- your mortgage company,
- your energy company,
- your mobile phone company,
- your house and car insurers and the like.
If you've got a complex home setup with servers and other machines which would be unfamiliar to the executor of your Will, then entrust someone else with the information required to revoke your keys, access your machines etc. and then provide the contact information for that person to your executor.
Arrange for your pets to be looked after.
Describe how you would like your belongings to be handled - do you want every effort made to have your clothes and furnishing recycled instead of going to landfill?
Where are the documents for the oven, the dishwasher and the central heating system so that these can be included in the sale of your property?
If there are loans outstanding, make sure your executor or a trusted person knows where to find the account numbers and company names.
What about organ donation? Make sure your executor knows your wishes and make sure your loved ones either agree or are willing to respect your wishes.
Then the personal stuff, what do you want to happen to your social media accounts, your cloud data, your games, DVD and CD collection, your photos and other media? Some social media companies have explicit settings available in your account to describe if you want the data deleted after a certain amount of time, after a notification from some government service or to set up some kind of memorialised version or hand over control of the account to a trusted person.
Next.